
If you're new to ShadowTrackr, this is the place to start. We'll discuss some important concepts like attack surface and online footprint. You'll learn how and why you should add assets, alerts and tags, and we'll explain the value of keyword monitoring for datadumps and newssites.
Your online footprint consists of everything that can be found on you online. For a typical business, this is a website with related infrastructure such as webservers, mailservers, webapplications and remote login services. When you have an insecure certificate on your website your visitors (and that includes your customers) will see a security warning instead of your website. If your webserver or mailserver has an insecure configuration, hackers will abuse it to send SPAM, host malware or even to attack others. This will result in your server appearing on blacklists which in turn will result in visitor seeing a security warning instead of your website again. Insecure webapplications and remote login services like Citrix, Juniper, TeamViewer or VNC are the main entrypoints for hackers that deploy ransomware. In short, clients and business partners will at some point notice if things are insecure, and this will reflect poorly on you. So, you should carefully track your online footprint. This practice is often referred to as “attack surface management”.
Besides your assets, there are the things you have less control over. Thinks articles about you in the news or data leaks and other sensitive information about your business that is dumped online on copy-paste sites. This doesn't have to be leak at your own organization, a supplier can have a leak that includes your data and this can affect you when the data appears on a site like pastebin.com.
Your attack surface is the part of your online footprint that can be used to further hack and exploit you and over which you yourself often have some form of control. You can fix the security problems on your website, and you can have your server removed from blacklists. ShadowTrackr will help you find and track your attack surface and show your weak spots as red dots on a map: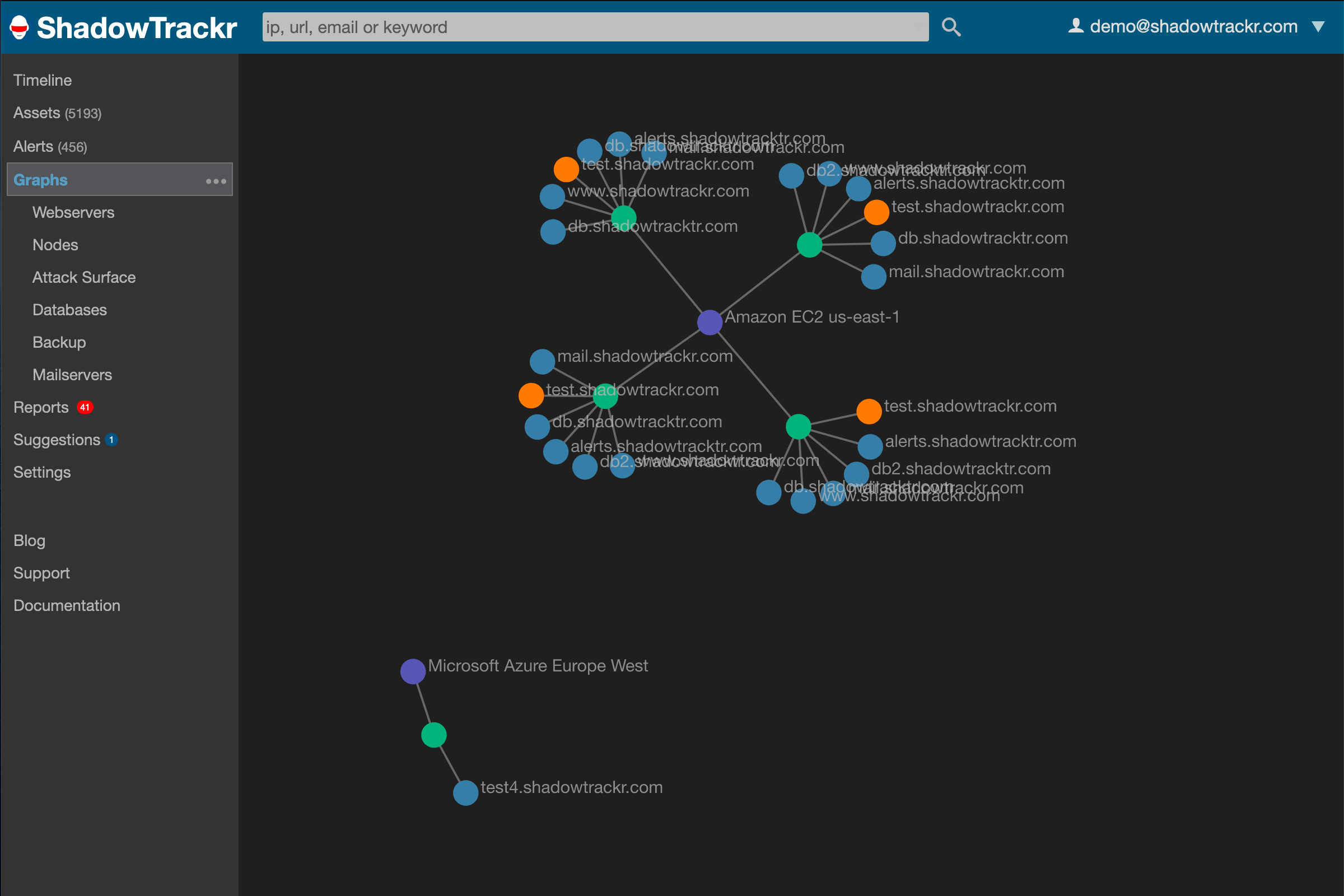 If you click the red dots, you'll see what is wrong and get some information on how to start improving. Alternatively, you can see all changes happening in real time on the ShadowTrackr timeline.
If you click the red dots, you'll see what is wrong and get some information on how to start improving. Alternatively, you can see all changes happening in real time on the ShadowTrackr timeline.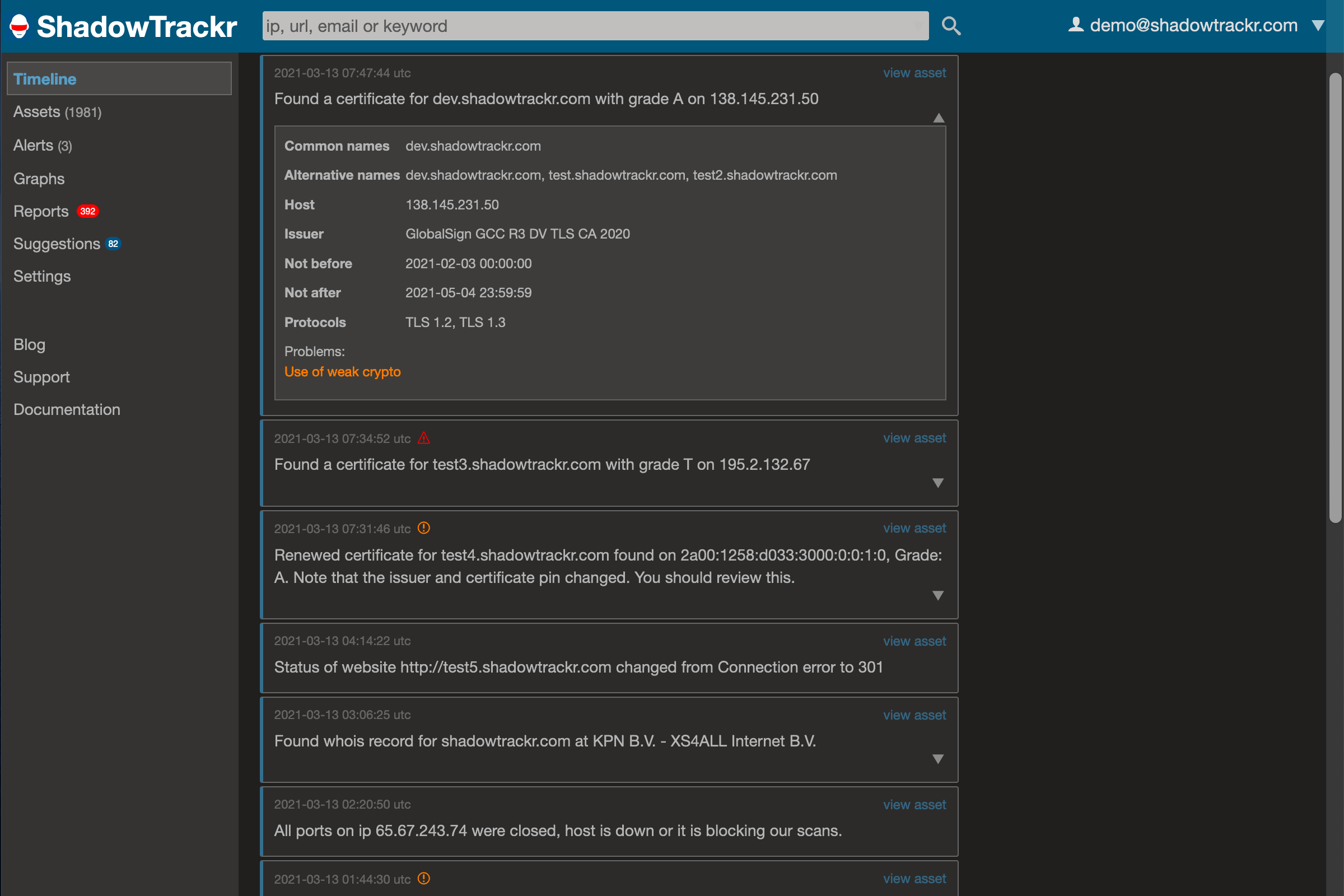 For those things in your online footprint you have less control over, ShadowTrackr can at least make sure you are the first to know when things go bad. You might not be able to prevent your sensitive information being dumped online, but at least you win some time to prepare and properly handle the fallout if you know in time. Anything related to your attack surface (like your domains) is monitored automatically. For the rest you can set alerts (more on that below here).
For those things in your online footprint you have less control over, ShadowTrackr can at least make sure you are the first to know when things go bad. You might not be able to prevent your sensitive information being dumped online, but at least you win some time to prepare and properly handle the fallout if you know in time. Anything related to your attack surface (like your domains) is monitored automatically. For the rest you can set alerts (more on that below here).
Your assets are your urls and ip addresses. Every website has a url (like shadowtrackr.com), but often find that you'll have more urls than websites. You'll likely have a mailserver. Maybe a nameserver. A remote login server. And how about that internal server for which the url should not appear on the internet? ShadowTrackr will find all these for you, but you'll have to provide a starting point. The best way to start is by entering your top level domain under assets: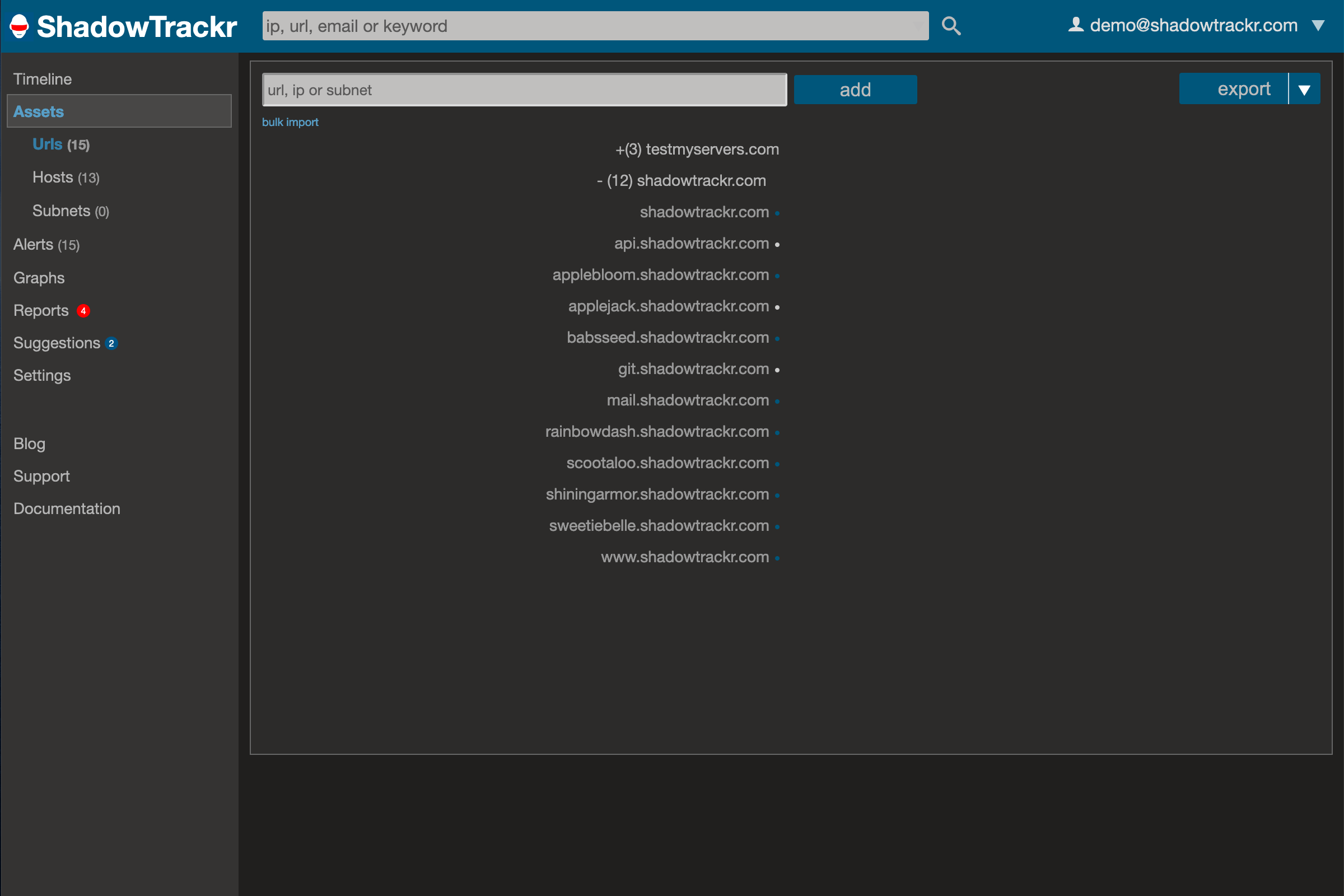 From that single url Shadowtrackr will start to expand and add urls, ip addresses and related data. Sometimes it's not clear if newly found assets are related to you or not (your website might run on shared hosting). When this happens, you'll get suggestions that you can accept or reject.
From that single url Shadowtrackr will start to expand and add urls, ip addresses and related data. Sometimes it's not clear if newly found assets are related to you or not (your website might run on shared hosting). When this happens, you'll get suggestions that you can accept or reject.
Along with urls, you can also add ip addresses. These will be found automatically for the urls you enter, but you might have ip addresses that are not related to a specific url. Think of your office internet connection. It'll likely be used for internet access only, especially for branch offices or home offices. But what if it appears on a hijacked pc, botnet or SPAM blacklist? What if some branch office decides to use all their computers to mine Bitcoin outside office hours? You'll want to know and that is why you should have all your internet connection ip addresses as assets in ShadowTrackr: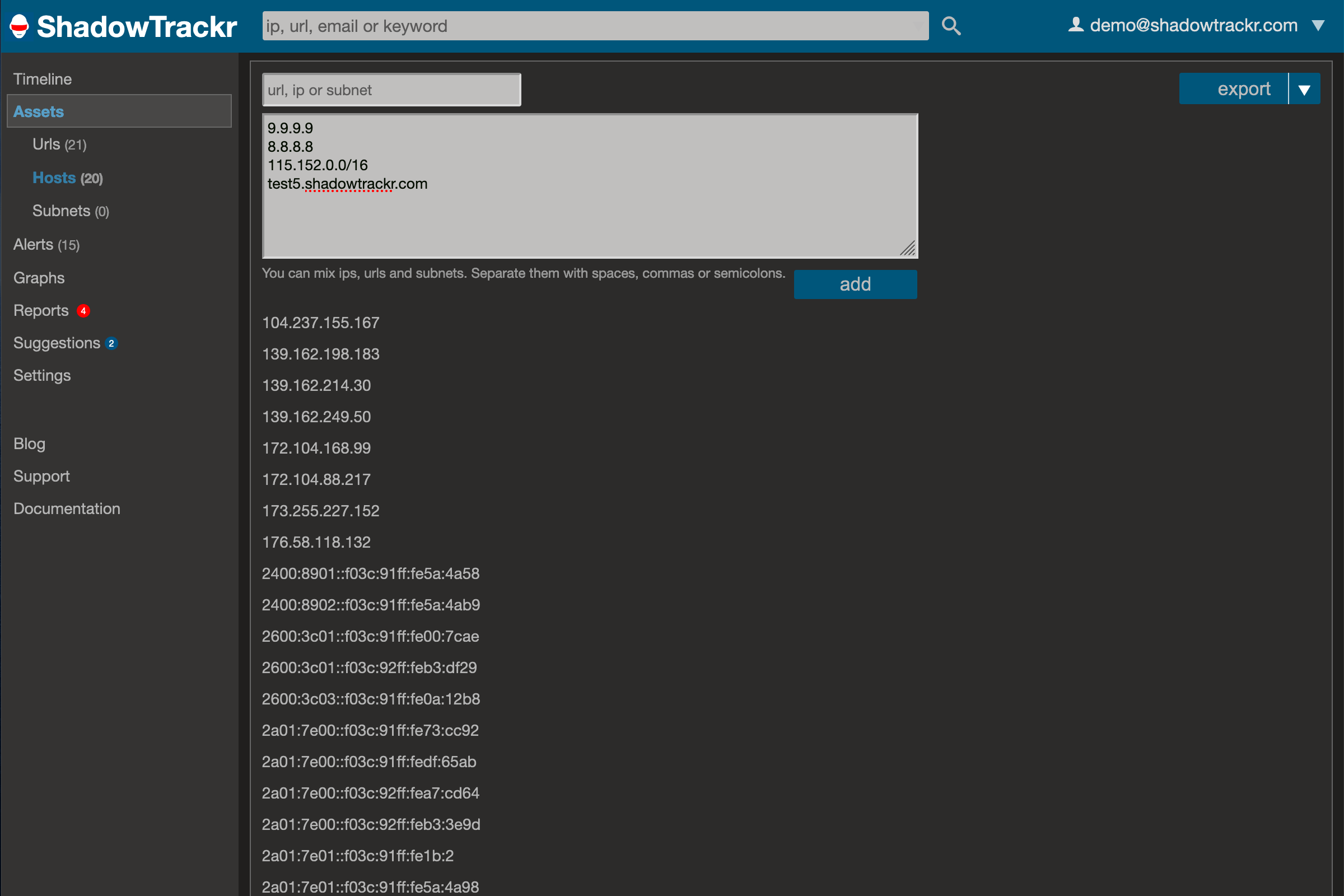 Other cases where you might want to monitor a specific ip address in ShadowTrackr are Building Management Systems or other IoT like devices, and shared hosting servers you want to watch (these will be suggested to you if you don't add them yourself).
Other cases where you might want to monitor a specific ip address in ShadowTrackr are Building Management Systems or other IoT like devices, and shared hosting servers you want to watch (these will be suggested to you if you don't add them yourself).
If you have a premium or enterprise subscription, you can even have entire subnets monitored. All ip addresses in the range will be regularly probed and if they are found to be up they will be automatically added and further processed.
If used well, your alerts will form a very effective early warning system. There are several types of alerts you can set: Events, keywords and canary tokens. We'll talk about the first two here. Canary tokens are an awesome free service provided by Thinkst. You can read up on them here and find out how to integrate them in ShadowTrackr.
You should start with adding some names and specific terms as keywords. For each keyword, you can choose if you want it monitored in datadumpsites and several categories of newsites. Email addresses and passwords of hacked accounts are regularly dumped on copy-paste sites like pastebin.com. Also, developers sometimes accidentally check in API secrets and other tokens in on online code repositories like GitHub.com. Since we already automatically monitor all your domains in all datasources, you don’t need to add extra keywords for this. The things you want to add here are company specific terms for internal classifications found in sensitive data (like “ShadowTrackr Confidential”), and things that might appear in the press if you have a dataleak (“ShadowTrackr hacked”).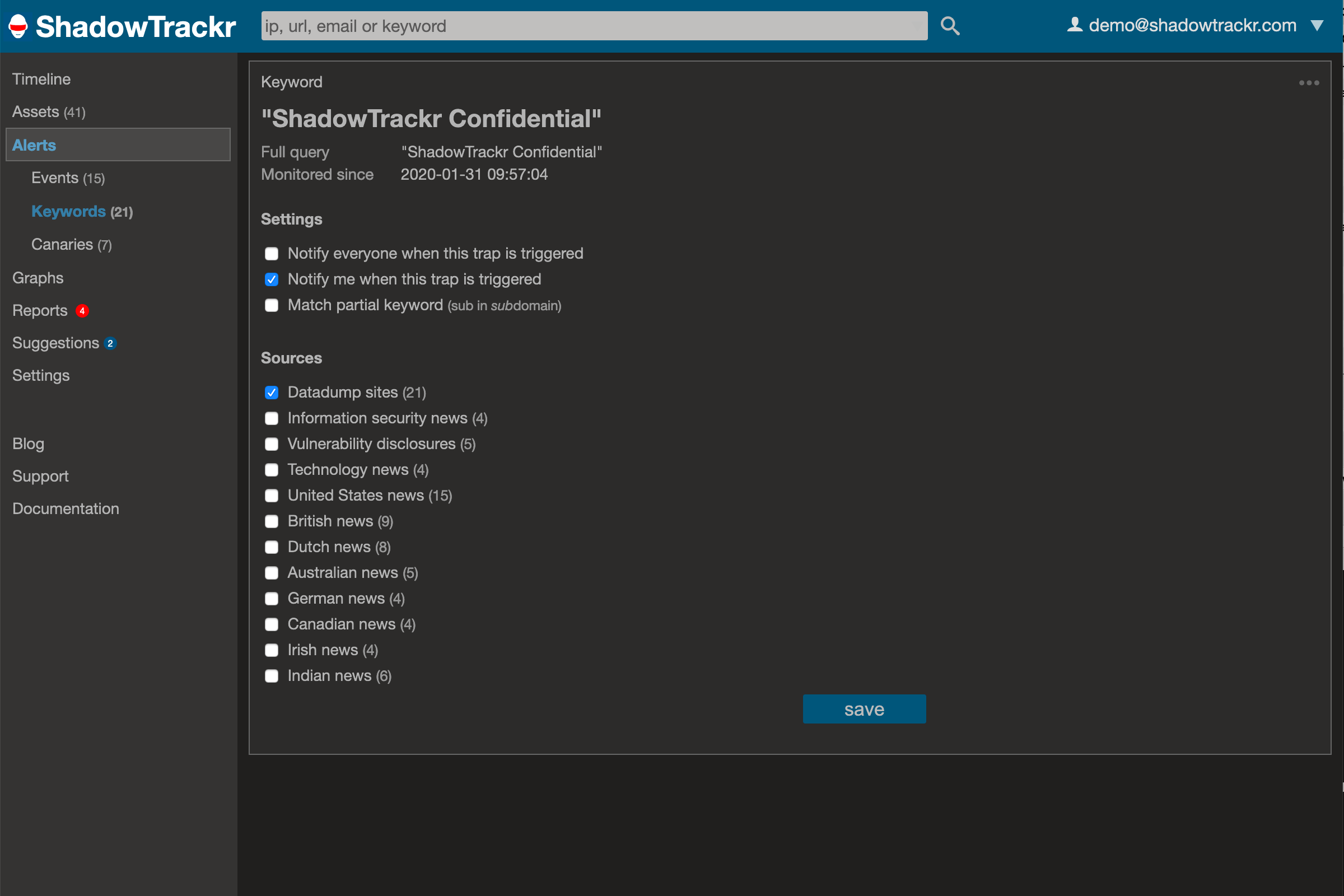 You can also add the names of publicly exposed persons like the CEO, CFO and other VIPs.
Any texts containing the name will be found. In our experience these are mostly either writers preparing an article or forum post, or evil scriptkiddies that try to dox you. Doxing is the jargon for publicly exposing all sorts of personal data you rather keep private. ShadowTrackr, or any other tool, can't prevent the doxing itself but at least you'll be the first to know.
You can also add the names of publicly exposed persons like the CEO, CFO and other VIPs.
Any texts containing the name will be found. In our experience these are mostly either writers preparing an article or forum post, or evil scriptkiddies that try to dox you. Doxing is the jargon for publicly exposing all sorts of personal data you rather keep private. ShadowTrackr, or any other tool, can't prevent the doxing itself but at least you'll be the first to know.
You can get very creative with keyword monitoring. If you suspect a document has leaked, use a very distinct and quotable part of a sentence from the document as a literal keyword and see if it turns up in the news or on a datadumps site. Or if you write software and are afraid your proprietary source code might be dumped online, you can have ShadowTrackr monitor some very distinct parts of your code on copy-paste sites.
Besides keyword alerts you can set alerts for events. Events are things that happen to your assets. A TLS certificate expiring on your website, a security configuration on your webserver, an internal database accidentally exposed to the internet, an insecure port opening on a server. There are many alerts you can set yourself. We’ve pre-configured the most useful alerts in your account, so you can start by fine-tuning those. Don’t be scare you mess things up, there is an easy button for that case (“reset user alerts”) under user management.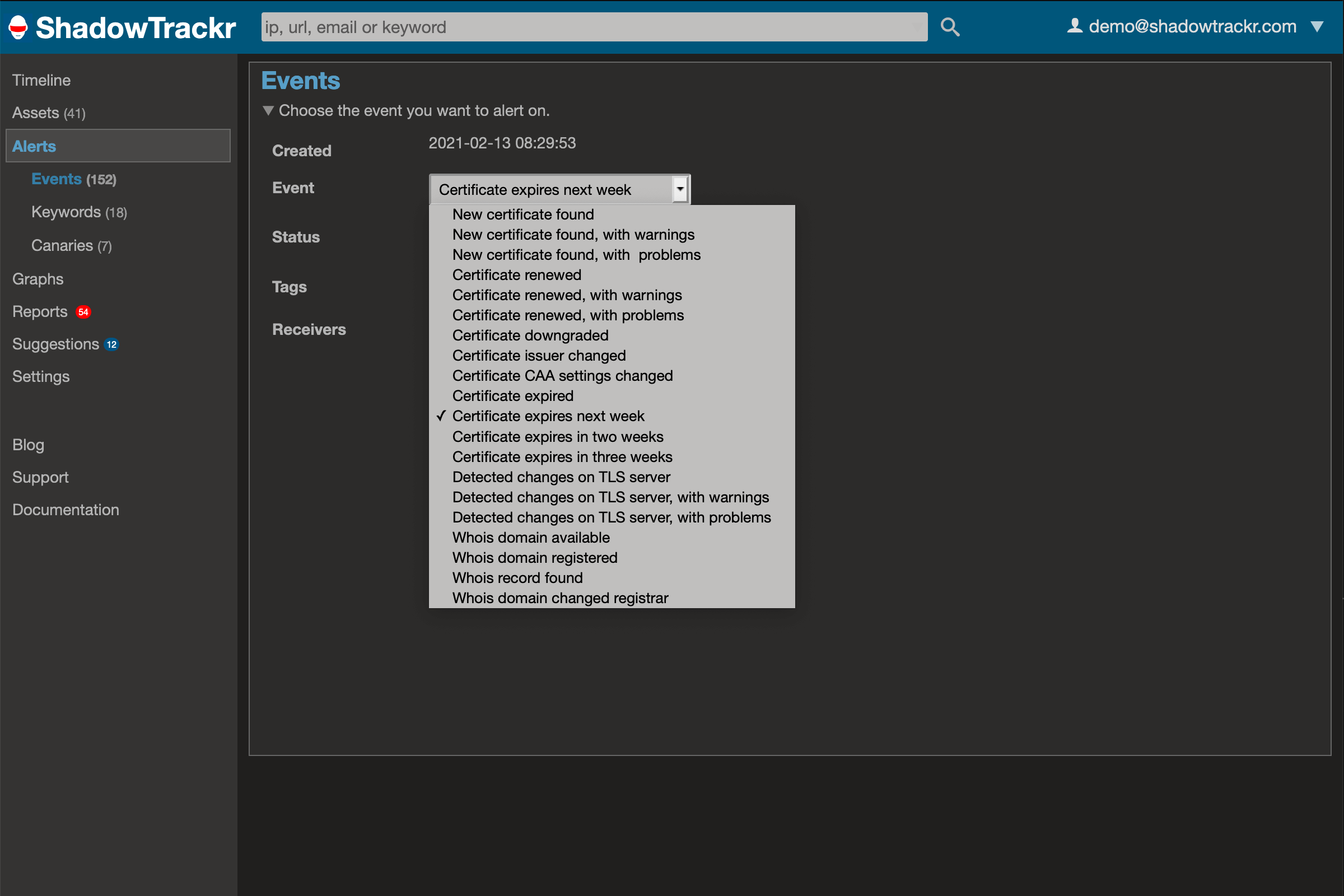
For larger organisations the number of assets can grow quickly. If you have thousands of assets you will want to prioritize and focus on the most important ones first. Tags allow you to label these important assets. How you divide things is completely up to you and you can choose your tags freely. Maybe you want to tag and group central infrastructure like mailservers and remote login servers and put them in a separate graph. Or maybe you want to receive alerts for every externally visible configuration change on your main website (you can use the tags in custom alerts for events).
Sometimes ShadowTrackr finds assets that are attached to your infrastructure but that are not of your concern. Since they are actually attached to you, you can’t remove them. Well, you can, but our scanning nodes will automatically find and add them again. This mostly happens at service providers. If you run the main domain and website for another company and they have a subdomain with a login at a branch office that they manage themselves, you might want to ignore that subdomain. You can do this with ignored urls or ignored host. You can even specify that all new domains appearing on a specific subdomain in the future will be ignored too. Be careful to not throw away the baby with the bathwater here. Is it really that bad when you detect a security issue on that clients own server and can warn them?
Now that you have seeded ShadowTrackr with urls and ip addresses, and have set some first alerts, your attack surface graph and timeline should be growing. You should regularly check these for problems and fix them as soon as possible. In ShadowTrackr, problems are things you should fix right now. Warnings should be fixed too, but are not show stoppers and thus less urgent. A good way to keep track of problems and warnings is having the weekly report on your assets and traps send to you by email as a pdf. You can maintain a mailing list for this under reports.
For the very worst of problems, make sure you have enabled email alerts or have installed the app and enabled notifications. This way, you'll get a push message for acute security problems or alerts that fire. Note that push messages are only send for those alerts where you have specifically enabled this. We don't want you to stop paying attention to the important stuff, so you should be selective here.
<- back to FAQ