
Ever heard of the canaries that miners took with them in coal mines? These little birds are more sensitive to dangerous gasses than humans. If a canary suddenly died the miners knew there was a dangerous gas leak, and still had time to get out. Canary tokens are the digital version of this. You hide them on your server, laptop, website or even in your mailbox. When they are used, you know something is wrong.
If you want to know more about canary tokens, read this introduction to Canary tokens on the Thinkst blog. You can create canary tokens for free on canarytokens.org. The process is simple and fast.  Now that you have made one, how will you know it was triggered? And how do you keep track of all your tokens? This is where integrating with ShadowTrackr will help. When you create a canary token, you can have it send an email or call a webhook when it fires. You can create webhooks in ShadowTrackr under traps. ShadowTrackr will show all canary activity on your timeline and can send push messages to your phone when a canary fires. And if you have multiple canaries, you'll have them nicely organized in one place.
Now that you have made one, how will you know it was triggered? And how do you keep track of all your tokens? This is where integrating with ShadowTrackr will help. When you create a canary token, you can have it send an email or call a webhook when it fires. You can create webhooks in ShadowTrackr under traps. ShadowTrackr will show all canary activity on your timeline and can send push messages to your phone when a canary fires. And if you have multiple canaries, you'll have them nicely organized in one place.
Here's the 3-step process:
Note that the webhook you create in ShadowTrackr is only activated after you save it. If you have trouble deciding what canaries you should plant, here are some ideas to get you started.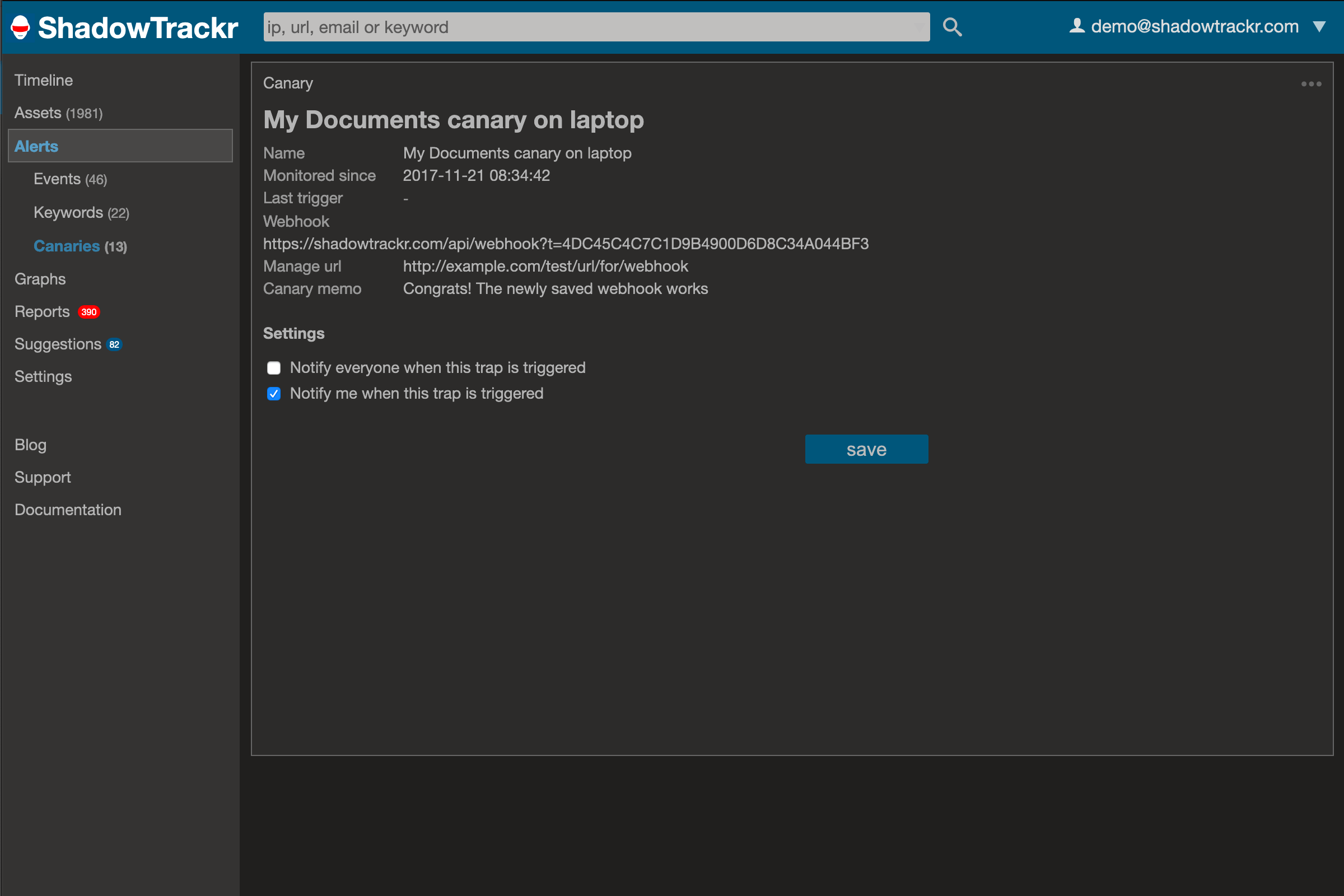
This is the most versatile canary that you can deploy almost anywhere, and you don't need any help from IT to do it. There are two options: A Word document that will send a message when opened, or a PDF file. The PDF file might not work beyond Acrobat Reader and not everyone has that installed. Word has a larger installed base and you'll have a bigger chance the canary works with it.
Start with a document that looks interesting and put it in your My Documents folder. Name it "Vulnerability overview.docx", "Annual performance bonus plan.docx", "Password.docx" or anything else that will entice people to open it. Remember to put some fake info in it to prevent your attacker from getting suspicious.
Save this document in a shared folder and instruct people not to open it (tell about the canaries), in personal folder on your laptop or work desktop (you know not to click it right?), or even in corporate document management system. Now if someone is snooping around, you will get a message instantly. There will also be some attacker information available like the ip address and browser version.
Add the email address you've created on canarytokens.org as a user account in a system where your clients or employees login. Think of webportals, webshops or remote work servers. If someone hacks that system, steals the email addresses and starts sending evil email you'll get a message.
You can also add a canary email token in a sensitive mailing list. Think of mailing lists in a marketing department that someone might want to use in a new job at your competitor. Remember to remove the canary before actually sending out a mailing, or at least inform the person monitoring ShadowTrackr that the canary will fire.
<- back to FAQ