
So, you have TLS certificate problems. We'll discuss why it's bad, where you can get certificates, and how to fix your problems. The security problem can be on the certificate itself (in which case you need to get a new one) or in the server configuration (in which case you need to change some settings and can go on with the same certificate). You'll also learn about forward secrecy (good) and certificate pinning (be careful with this!).
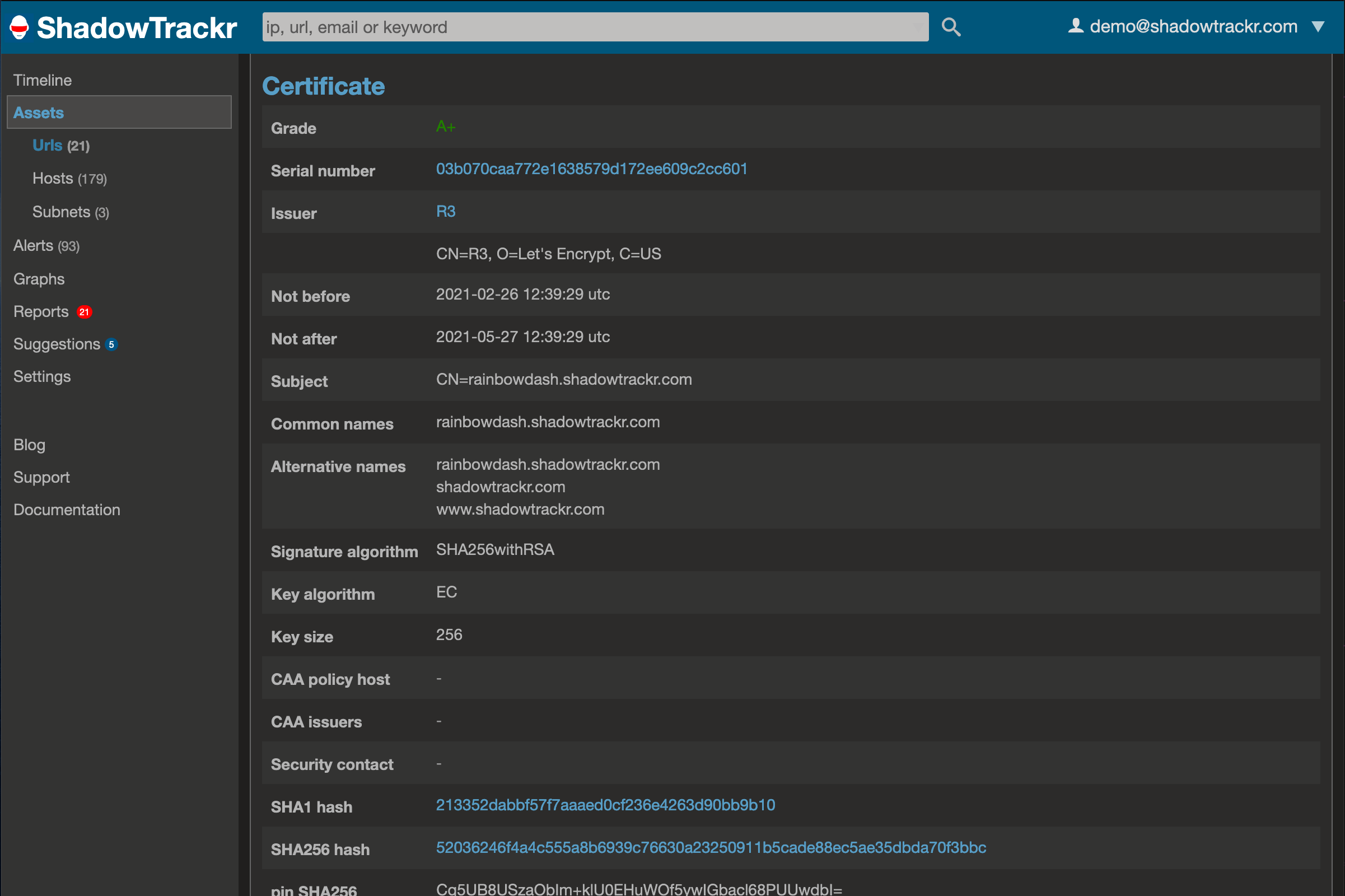
There are quite a few ways to get it wrong and you'll easily get lost in the crypto jargon. To deal with this, SSL Labs came up with grades. The grade is for a combination of the certificate (issued for a url) on a specific webserver (with an ip address), and that's how we process stuff in ShadowTrackr as well. That means that if you have a website you load balance over two servers, you will have two certificates for that website (unless you don't do round robin and somehow serve only the same one to all our nodes). Here's an overview of the grades:
| Grade | Meaning |
|---|---|
| A-, A or A+ | You're good |
| B or C | Not urgent, but you should improve |
| D or E | You are insecure, fix it |
| F, T or M | You are very insecure, drop everything and fix it now |
Note that there are two effects for insecure certificates, especially those below a B:
There are several categories of problems you can have with your certificate and even if you have just one of these you need to get a new, better certificate:
There are broadly three categories of problems you can have on your server:
In all these cases you need to fix your server, not the certificate. Confused about what secure settings are? Check the TLS deployment best practices over at SSL labs.
Although this is cryptographically quite complicated, the simple result is that if you have forward secrecy, any compromise of your private key in the future will not lead to the attacker being able to read your past messages.
If you don't have forward secrecy, this means that if an attacker saves your traffic today and steals your private key tomorrow, he can (tomorrow) decrypt tomorrow's traffic, today's traffic and anything earlier if that was saved too. In short: you want to limit the impact of theft and have as much forward secrecy as possible.
Certificate pinning, which is the same as public key pinning, is a trick where your website states (in a security header that is part of HTTP) which public keys should be used on your certificate. This prevents abuse like with the Diginotar hack in 2011.
Your browser normally visits the website, checks the certificate, decrypts the page and then sees the pinned public key in the security header. The first time it sees the pinned public key, it saves if for the period you have specified in max-age. In this example, it's a day:
Public-Key-Pins: pin-sha256="[TheKey]"; max-age=86400
Every next time that browser visits your website during the specified period, it will refuse to show the page if the public key on the certificate does not match the one it has saved earlier. Sound ok right? The thing is, if you specify a pin that is valid for 10 days and mess up, no one can visit your website during those 10 days!
You can mess up by loosing your private key (generating a new one will mean you have a new public key) or just simply making a typo when you configure the header on your server. Because of this risk, some browsers (like Chrome) don't think it's good trick and have stopped supporting it. You can still use it, but if you do please guard your private key with your life and use a reasonably short time period in max-age.
You get a certificate from a Certificate Authority. You can go all out and buy expensive certificates. The seller will claim that they support the most devices (like refrigerators or other uncommon edge cases) and will try to upsell you by offering extended validation. Don't fall for it, as Troy Hunt explains here: extended validation is dead.In most cases is good enough to just go for a free (as in beer and speech) certificate from the great people at Let's encrypt.
ShadowTrackr gathers and saves all certificates we can find for your urls and ip addresses. We read them directly from your servers and check external sources like certificate transparancy logs for anything related to your assets. You'll get messages when someone issues a new certificate for your url, if your certificate expires (from 3 weeks before), if your certificate grade changes and more. The important changes and current problems also appear in your weekly report.
If you want to upgrade your certificates, you'll find an overview in the certificate report. Just click on the part of the pie with the lowest grades and you'll have the list of certificates that you need to start with. There is a convenient export to Excel option as well.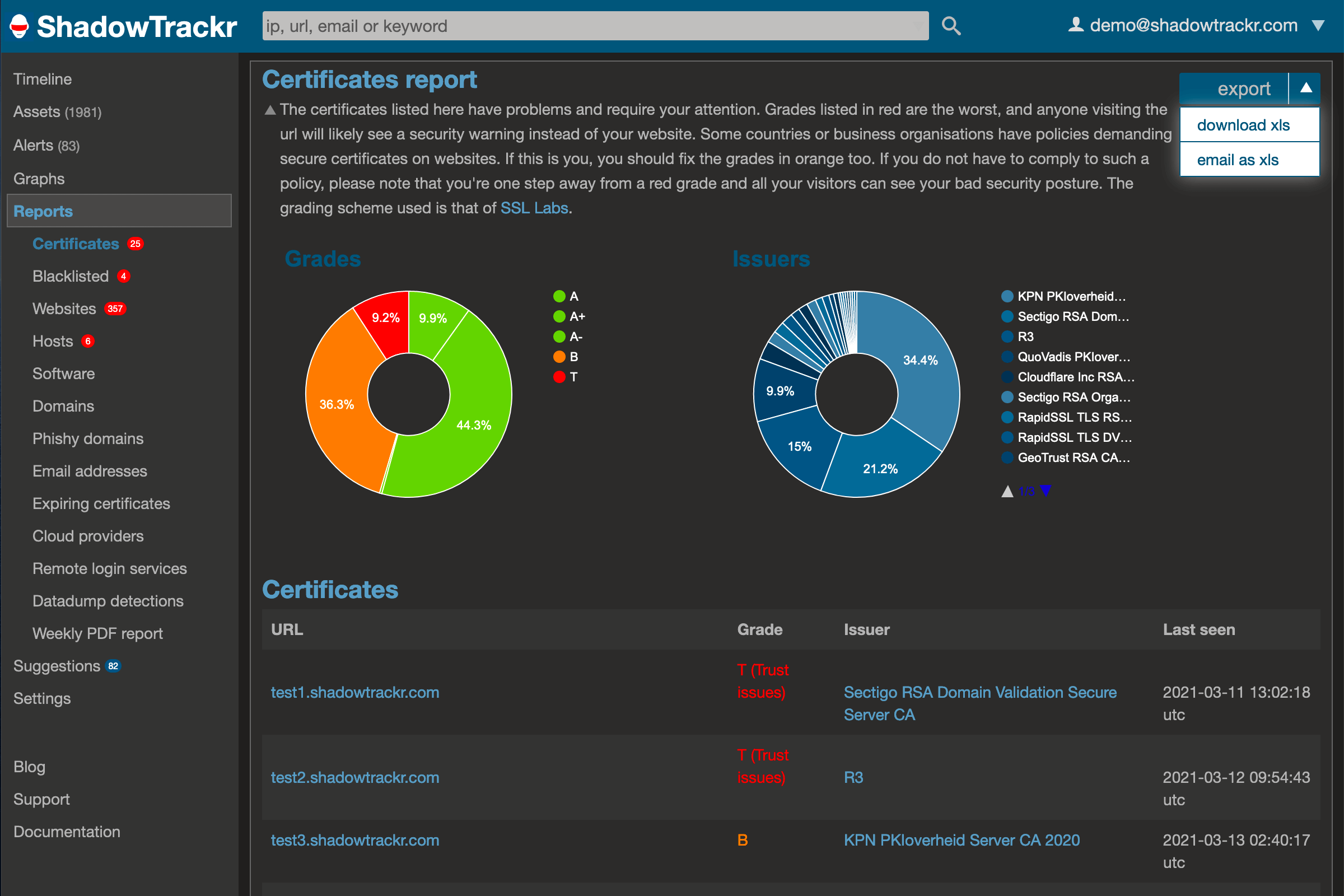
<- back to FAQ